June 6, 2025 – President Donald Trump lauded a significant agreement on spectrum allocation, praised as the “largest spectrum pipeline ever,” brokered within the budget reconciliation text by key Republican senators. The deal, projected to raise an estimated $85 billion for U.S. taxpayers, aims to solidify American global leadership in wireless technologies, including the nascent 6G frontier.
In a statement posted on Truth Social, President Trump specifically congratulated Senator Ted Cruz (R-Texas), Chairman of the Senate Committee on Commerce, Science, and Transportation, for his leadership on the provision. He also acknowledged the collaborative efforts of Senator Roger Wicker (R-Miss.), Chairman of the Senate Committee on Armed Services, and Senator Tom Cotton (R-Ark.), Chairman of the Senate Republican Conference and Senate Select Committee on Intelligence, for their roles in forging the bipartisan-backed agreement.
“Congratulations to Chairman of the Senate Committee on Commerce, Science, and Transportation, Ted Cruz, Chairman of the Senate Armed Services Committee, Roger Wicker, and Chairman of the Senate Republican Conference, Tom Cotton, for their amazing deal on Spectrum as posted last night,” President Trump wrote. “This is serious power for American Leadership on 6G. We will have the World’s Greatest Networks, and ensure the Highest Level of National Security for future Generations of Americans.”
According to the Commerce Committee, the spectrum provision is designed to convert unused and underused spectrum into private sector assets, which is expected to unleash billions in private investment and create thousands of new jobs. Proponents argue that increased spectrum auctions will lead to cheaper and faster internet for consumers and foster the development of new AI-enabled technologies, driving productivity growth across the economy.
President Trump also used the announcement to draw a sharp contrast with the previous administration. “Biden did nothing on Spectrum in four years,” he stated, before asserting, “but, thanks to ‘THE GREAT BIG BEAUTIFUL BILL,’ my Administration will beat all expectations, and show the World the path forward!”
The agreement underscores a key legislative victory for the Republican-led Senate and the Trump administration, positioning the United States to accelerate its technological competitiveness and enhance its national security posture in the rapidly evolving global wireless landscape.
What Makes Wireless Work? An Explanation of Spectrum Allocation
Wireless communication relies on the electromagnetic spectrum, an invisible range of radio frequencies that transmit data through the air.
What does “spectrum” refer to in the context of wireless technology?
The “spectrum” in this context refers to the electromagnetic spectrum, which includes different types of waves like radio waves, microwaves, infrared, and more. Think of it as a big highway where various types of vehicles (data and signals) travel at different speeds (frequencies). This spectrum is vital for everything from cellphones to Wi-Fi!
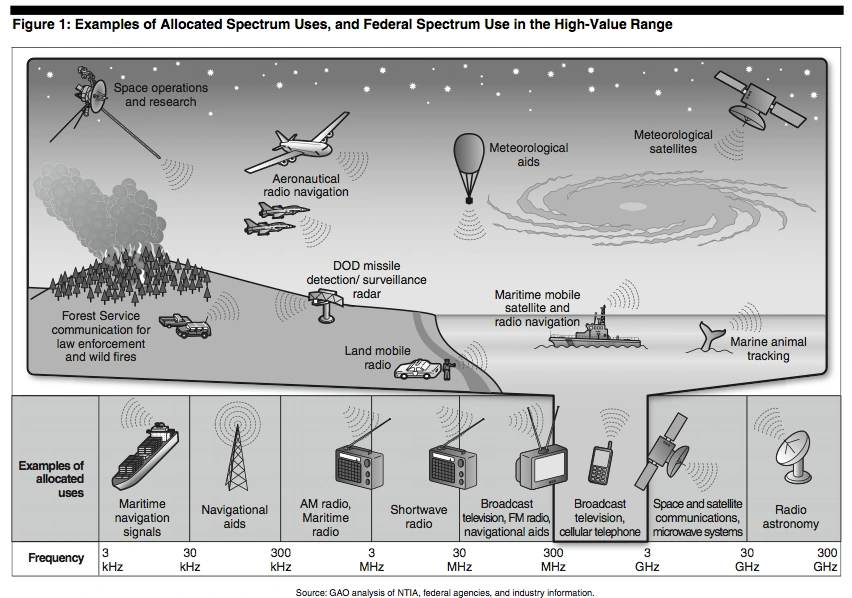
Explaining Spectrum Allocation
Spectrum allocation is the process by which regulatory bodies assign specific portions of the radio spectrum, known as bands, for different applications and services. In the United States, the Federal Communications Commission (FCC) is the primary independent agency responsible for this task, managing allocations for broadband, public safety, and media. Similarly, the National Telecommunications and Information Administration (NTIA) manages spectrum use for federal government agencies.
Historically, spectrum allocation has evolved significantly. Early methods included “beauty contests” or comparative hearings, where firms presented their cases to the FCC, and lotteries, which aimed to provide equal opportunity but often led to speculative behavior. However, since 1994, auctions have become the predominant method for allocating licensed spectrum in the U.S. and over 100 other countries. Auctions allow market forces to determine the most valuable uses of spectrum, generating significant revenue for governments while incentivizing the efficient deployment of new technologies
How do wireless connections work?
How do our devices use the electromagnetic spectrum?
Devices like cellphones and Wi-Fi routers communicate by sending and receiving electromagnetic waves at specific frequencies—which we can think of as different lanes on a highway. These waves carry digital information (think 0s and 1s, like a Morse code) that your device encodes and decodes so you can hear people on the phone or stream videos online.
What are spectrum bands and how are they organized?
What are spectrum bands?
Spectrum bands are individual ranges of electromagnetic waves designated for certain uses like radio, television, or mobile communications. Just as a city decides which streets are for buses and which are for cars, regulators assign specific frequency bands for different uses to reduce interference from other signals.
What are the different frequencies and their characteristics?
How do frequency bands differ?
- Low-band spectrum: Travels further distances with less interference, making it great for covering large areas (like cell towers).
- Mid-band spectrum: Balances coverage and capacity, ideal for fast technologies like 5G.
- High-band spectrum: Can carry more data, but has a shorter range and is more susceptible to interruptions.
Why is spectrum allocation crucial?
What is spectrum allocation and why do we need it?
Spectrum allocation is how regulators divide the electromagnetic spectrum into frequency bands for various services to prevent overcrowding. Imagine a busy park: if everybody uses the same patch of grass, it becomes chaotic. Proper allocation helps keep things organized and ensures important signals aren’t disrupted.
Who manages spectrum in the U.S.?
What agencies are responsible for regulating the spectrum in the US?
- Federal Communications Commission (FCC): Oversees telecommunications regulations for commercial uses.
- International Telecommunication Union (ITU): A global body that coordinates international use of the radio spectrum among member countries.
What is the difference between licensed and unlicensed spectrum?
- Licensed spectrum: Exclusive access to certain frequencies granted to specific users like mobile companies, ensuring they have reliable service.
- Unlicensed spectrum: Open for anyone to use without exclusive rights (like Wi-Fi), but it can get congested and less reliable.
Beyond exclusive licensing, spectrum is also allocated for:
- Unlicensed Use: These bands are open to anyone who adheres to specific technical rules, such as power limits, without requiring individual licenses. Technologies like Wi-Fi and Bluetooth operate in unlicensed spectrum, fostering innovation and lowering barriers to entry for various devices and applications.
- Shared Spectrum: This approach allows multiple users to access the same band under dynamic or coordinated rules, aiming for more efficient use of limited frequencies. The Citizens Broadband Radio Service (CBRS) in the 3.5 GHz band is a notable example, where commercial mobile users operate underneath naval radars with priority.
The choice of allocation method depends on various factors, including the specific frequency band’s characteristics. Lower frequency bands offer wider coverage but lower data capacity, while higher frequency bands (like millimeter wave, mmWave) provide extremely high capacity and low latency but have limited coverage
How does shared spectrum work?
What is shared spectrum?
Shared spectrum is a newer concept where multiple users can operate on the same band under certain rules. For instance, the utilized frequency band might allow the Navy to use it without interference while still permitting others when not in use. This is like a community park that allows multiple events as long as they don’t overlap.
Limitations of Present Spectrum Allocation
Despite the advancements in spectrum management, several limitations continue to exist:
- Political and Bureaucratic Inertia: The process of reallocating spectrum can be highly contentious and politically challenging. Federal agencies, particularly the Department of Defense (DOD), often resist relinquishing underutilized bands, even when they could be more productively used for commercial purposes. This gridlock can significantly delay the deployment of new wireless infrastructure and technologies like 5G and 6G.
- Lapse of FCC Auction Authority: As of March 2023, the FCC’s authority to auction spectrum for commercial deployment has expired. This lack of a defined plan for allocating additional licensed spectrum creates uncertainty for commercial users and puts the U.S. at a disadvantage in global wireless leadership.
- Spectrum Crunch and Global Competition: The U.S. faces a tangible spectrum crunch, trailing other leading countries in spectrum availability, especially in mid-band spectrum crucial for modern telecommunications. China, for instance, has been decisive in clearing and allocating mid-band spectrum, positioning itself to lead in equipment standards for 5G and beyond. This disparity can have significant national security implications, as it affects the development of trusted supply chains and the ability of U.S. and allied technology to compete globally.
- Suboptimal Allocation Balance: While unlicensed spectrum has driven significant innovation and economic value (e.g., Wi-Fi), an excessive reliance on it for critical infrastructure can be problematic. Unlicensed spectrum, by nature, offers less reliability due to potential interference and overcrowding, making it less suitable for applications requiring guaranteed service, such as industrial IoT or critical enterprise uses. Some argue that the disproportionate focus on unlicensed spectrum in the U.S. has been a strategic blunder, as other countries have allocated more licensed spectrum for 5G, leading to a lack of global harmonization.
- Interference and Reliability Concerns in Shared/Unlicensed Bands: While shared and unlicensed models aim to maximize spectrum use, they inherently involve trade-offs in reliability and interference management. The “price” of free access to unlicensed spectrum is the sacrifice of guaranteed protection from interference. Similarly, shared spectrum often comes with limitations, such as lower power levels, which can diminish its value for full-powered uses like nationwide mobile networks.
- Challenges in Private Network Spectrum Acquisition: For enterprises looking to build private 5G networks, the ability to acquire spectrum licenses varies significantly by geography. In some countries, enterprises can directly obtain licenses, while in others, only Mobile Network Operators (MNOs) can. This inconsistency can hinder global companies from deploying consistent private networks and limit the participation of other entities in the 5G market.
- Underfunded Research in Sharing Technologies: While dynamic spectrum sharing holds promise, the technological barriers to maximally efficient spectrum use remain. Projects like the Incumbent Informing Capability (IIC) are crucial for advancing sharing technologies but are often underfunded, delaying their widespread deployment and effectiveness.
Understanding the Risks of 6G Technology: The Next Cybersecurity Challenge

As we stand on the brink of a new technological era, the advent of 6G technology promises unprecedented speed, connectivity, and efficiency. While this next-generation wireless communication system is expected to revolutionize industries ranging from healthcare to smart cities, it also introduces new cybersecurity challenges. 6G technology risks must be carefully assessed to ensure this innovation does not become a gateway for cyber threats.
The Landscape of 6G Technology
6G is projected to be at least 100 times faster than 5G, with ultra-low latency and extensive AI-driven applications. It will enable real-time data processing, autonomous systems, and advanced quantum communication. However, with such capabilities come significant 6G security threats, including sophisticated cyberattacks, data breaches, and infrastructure vulnerabilities.
According to a report by MarketsandMarkets, the global 6G market is expected to reach $3.96 billion by 2030, indicating rapid adoption and widespread influence across industries (MarketsandMarkets, 2024). Additionally, cybercrime is anticipated to cost the world 15.63 trillion U.S. dollars by 2029, further underscoring the urgency of addressing 6G security risks (Statista, 2024).
Key 6G Cybersecurity Challenges
1. 6G Network Vulnerabilities
One of the biggest concerns with 6G network security is its decentralized nature. Unlike previous generations, 6G will leverage distributed networking and AI-driven automation, which may create network vulnerabilities that are difficult to detect and mitigate. Potential attack vectors include:
- Supply chain attacks: Cybercriminals targeting hardware and software suppliers can compromise the security of 6G infrastructure.
- AI exploitation: Since AI will play a crucial role in network management, adversaries may manipulate algorithms to disrupt operations.
- Quantum hacking threats: With quantum computing advancements, traditional encryption methods may become obsolete, making 6G more vulnerable to cyberattacks.
Considering the role of AI in cyberattacks, the potential risks associated with AI-driven automation in 6G are increasing.
2. 6G Data Privacy Concerns
With the increase in connected devices and the Internet of Everything (IoE) expansion, personal and enterprise data will be more exposed than ever. 6G data privacy concerns include:
- Massive data collection: Organizations and governments will have access to substantial amounts of personal data, raising ethical and legal concerns about privacy violations.
- Data interception risks: Hackers could exploit weak points in the network to intercept, alter, or steal sensitive information.
- Identity theft and deepfake threats: As AI integration grows, cybercriminals may use deepfake technology to impersonate individuals and manipulate data.
A survey by Statista found that the global average cost per data breach amounted to 4.88 million U.S. dollars, and with 6G handling exponentially more data, these costs could surge (Statista, 2024).
3. Emerging 6G Security Threats
The complexity of 6G introduces novel 6G security threats, including:
- Autonomous attack systems: AI-driven cyberattacks could launch large-scale, automated threats that adapt in real-time.
- IoE exploitation: Connected devices in homes, workplaces, and critical infrastructure will be vulnerable to cyber intrusions.
- Nation-state cyber warfare: Governments may use 6G to conduct espionage or sabotage rival nations’ digital infrastructure.
A World Economic Forum report indicates that 93% of cybersecurity leaders believe that geopolitical instability will lead to a disastrous cyber event in the next two years, making 6G a critical concern (World Economic Forum, 2023). Mitigating 6G Technology Risks
While the cybersecurity landscape of 6G presents numerous challenges, implementing 6G security solutions can help mitigate risks and ensure safer adoption.
1. Enhanced 6G Data Encryption:
Encryption will be a 6G network security cornerstone. Key strategies include:
- Post-quantum cryptography (PQC): Developing encryption methods resistant to quantum attacks will be crucial.
- End-to-end encryption: Ensuring that all data transmissions are securely encrypted from the sender to the receiver will reduce interception risks.
- Blockchain integration: Decentralized blockchain authentication can prevent unauthorized data access and manipulation.
2. AI-Driven Threat Detection:
Since AI will be integral to 6G, it should also be leveraged for cybersecurity, including:
- Real-time anomaly detection: AI-powered systems can identify and neutralize cyber threats before they escalate.
- Adaptive security frameworks: Machine learning algorithms can adapt to new attack patterns and develop countermeasures.
- Automated threat response: AI can detect and mitigate cyber threats without human intervention, reducing response times.
3. Regulatory Frameworks and Global Collaboration:
Addressing 6G cybersecurity challenges requires a multi-stakeholder approach, including:
- Global cybersecurity standards: Governments, tech companies, and regulators must work together to develop universal security standards for 6G.
- Ethical AI policies: Transparent guidelines should be established to regulate AI’s role in network security.
- Cross-border cooperation: International collaborations can help combat cybercrime and share threat intelligence.
As 6G technology ushers in a new era of digital transformation, understanding and addressing its cybersecurity risks is paramount. The 6G cybersecurity challenges surrounding network vulnerabilities, data privacy concerns, and emerging threats demand proactive security measures. By implementing 6G security solutions such as advanced encryption, AI-driven threat detection, and global regulatory frameworks, we can harness the benefits of 6G while minimizing its risks. The future of cybersecurity in the 6G era will depend on a collective effort to build resilient, adaptive, and secure communication networks.
Ref:
- MarketsandMarkets. (2024, September). 6G Market by Enterprise Application (Holographic Communication, Tactile/Haptic Internet, Fully Automated Driving, Industry 5.0, Internet of Bio-Nano-Things, Deep-sea Sightseeing), Usage Scenario (FeMBB, ERLLC, umMTC, LDHMC, ELPC) – Global Forecast to 2035. Retrieved from https://www.marketsandmarkets.com/Market-Reports/6g-market-213693378.html
- Statista. (2024, July 30). Estimated cost of cybercrime worldwide 2018-2029. Retrieved from https://www.statista.com/forecasts/1280009/cost-cybercrime-worldwide
- Statista. (Sep 11, 2024). Average cost of a data breach worldwide from 2014 to 2024. https://www.statista.com/statistics/987474/global-average-cost-data-breach/
- World Economic Forum. (2023, January 18). Geopolitical Instability Raises Threat of ‘Catastrophic Cyberattack in Next Two Years’. Retrieved from https://www.weforum.org/press/2023/01/geopolitical-instability-raises-threat-of-catastrophic-cyberattack-in-next-two-years/
- Good and Bad Reasons for Allocating Spectrum to Licensed, Unlicensed, Shared, and Satellite Uses [ https://itif.org/publications/2023/10/23/good-bad-reasons-for-allocating-spectrum-to-licensed-unlicensed-shared-satellite-uses/ ]
- Bandwidth allocation. [ https://en.wikipedia.org/wiki/Bandwidth_allocation ]
- More Spectrum, Please. [ https://www.rstreet.org/commentary/more-spectrum-please/ ]
- How the Allocation of Private Mobile Wireless 5G Spectrum Impacts Enterprises. [ https://isg-one.com/articles/how-the-allocation-of-private-mobile-wireless-5g-spectrum-impacts-enterprises/ ]
- Spectrum Allocations and Twenty-First-Century National Security. [ https://www.csis.org/analysis/spectrum-allocations-and-twenty-first-century-national-security/ ]
- Spectrum management: Key applications and regulatory considerations driving the future use of spectrum. [ https://digitalregulation.org/spectrum-management-key-applications-and-regulatory-considerations-driving-the-future-use-of-spectrum-2/ ]
- 6G: Cybersecurity Challenge[ https://www.eccu.edu/blog/understanding-the-risks-of-6g-technology-the-next-cybersecurity-challenge/]
Also Read:
