July 31, 2025: Airtel and Reliance Jio have begun enforcing mandatory facial authentication for Aadhaar verification during the issuance of SIM cards. This practice is currently being implemented at various retail locations in Chennai and is reported to violate guidelines from the Unique Identification Authority of India (UIDAI) and the Department of Telecommunications (DoT).
The facial authentication requirement has been observed in multiple retail outlets across Chennai, including regions such as Mogappair, Korattur, Anna Nagar, Adyar, and Ayanavaram. Customers seeking new SIM cards or replacements are required to undergo facial scans, with service denied if authentication fails or is declined.
- Violation of UIDAI Guidelines:
- UIDAI stipulates that facial authentication must be consent-based and part of a range of authentication options, which typically include:
- One-time passwords (OTP)
- Fingerprint scans
- Iris scans
- Customers have reported a lack of transparency regarding the purpose and process of facial authentication, often being asked to comply without proper briefing.
- UIDAI stipulates that facial authentication must be consent-based and part of a range of authentication options, which typically include:
Increased Vulnerability During Outages
During an outage, organizations might resort to less secure temporary alternatives to maintain operations, creating opportunities for attackers. This could involve reverting to password-based authentication without multi-factor authentication (MFA), which is more susceptible to brute-force attacks or phishing.

JANUARY 2025: AADHAAR-BASED BIOMETRIC VERIFICATION IS NOW MANDATORY FOR OBTAINING A NEW SIM CARD IN INDIA
The new Telecommunications Bill in India, which mandates biometric authentication for obtaining new mobile numbers and potentially for existing users, has faced opposition primarily due to concerns regarding privacy, proportionality, and the potential for exclusion. The primary identification method for this biometric authentication is expected to be Aadhaar, India’s national biometric identity system .
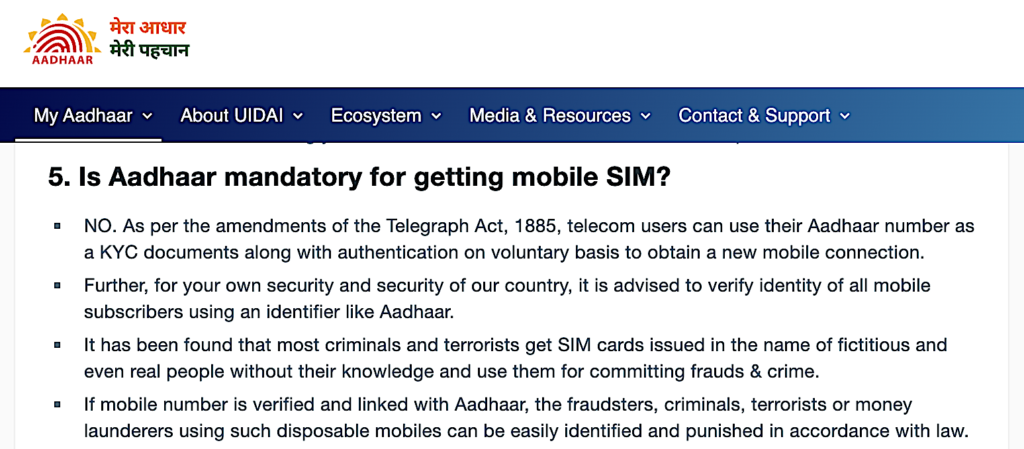
Is Aadhaar mandatory for getting mobile SIM?
UIDAI: NO. As per the amendments of the Telegraph Act, 1885, telecom users can use their Aadhaar number as a KYC documents along with authentication on voluntary basis to obtain a new mobile connection.
Opposition to the New SIM Card Rule
The opposition to the new SIM card rule largely stems from legal and civil liberties groups, privacy advocates, and some legal experts who argue that the mandate for biometric authentication, particularly through Aadhaar, infringes upon fundamental rights and raises significant questions about state surveillance.
Legal and Constitutional Challenges
A key point of contention is the Supreme Court of India’s landmark judgment in Justice K.S. Puttaswamy (Retd.) & Anr. vs. Union of India & Ors. (2017), which declared privacy a fundamental right under Article 21 of the Indian Constitution. This judgment established a three-part test for any state action that infringes on privacy: legality, necessity, and proportionality. Critics argue that mandating biometric authentication for SIM cards, especially for existing users, may not meet the proportionality test. Manmeet Kaur, a Partner at Karanjawala & Co., notes that the Supreme Court in the Puttaswamy judgment observed the linking of Aadhaar with mobile numbers as “disproportionate and unreasonable state compulsion”.
Abhay Chattopadhyay, Partner at Economic Laws Practice, highlights that while the Department of Telecommunications (DoT) previously allowed voluntary Aadhaar-based biometric verification, the new Section 3(7) of the Telecommunications Act mandates “verifiable biometric based identification” for all prospective subscribers. He suggests that this reversal of the previous voluntary stance will likely undergo further judicial scrutiny to ensure it falls within the parameters of the Puttaswamy judgment. The government will need to demonstrate a clear rationale for this mandatory requirement.
Concerns over Surveillance and Data Security
Civil society organizations and privacy advocates express apprehension that mandatory biometric authentication could lead to increased state surveillance and the creation of a comprehensive digital footprint of citizens’ communication activities. The continuous linking of a mobile number to an individual’s biometric identity, especially if extended to existing users, could enable real-time tracking and monitoring, raising fears about the erosion of civil liberties.
Furthermore, concerns about data security and the potential for breaches of sensitive biometric information are paramount. While the Aadhaar system has robust security measures, any system handling such a vast amount of personal and biometric data is a potential target for cyberattacks. A breach could have severe consequences, including identity theft and misuse of personal information.
Potential for Exclusion and Accessibility Issues
Critics also point to the potential for exclusion, particularly for individuals who may face difficulties with biometric authentication due to physical disabilities, age-related biometric changes, or lack of access to necessary technology. While the proposed framework includes fallback mechanisms like OTP verification and in-person checks, the primary reliance on biometrics could disproportionately affect vulnerable populations or those in remote areas with limited digital infrastructure. The 2011 Census of India indicates that over 2.21% of the population lives with some form of disability, and many may struggle with consistent facial recognition data.
Drawbacks of Aadhaar-based Biometric Verification for New SIM Cards
While Aadhaar-based biometric verification offers enhanced security and identity assurance, it also presents several drawbacks, particularly when mandated for new SIM card activations.
Single Point of Failure and Security Vulnerabilities
Relying solely on Aadhaar for biometric verification creates a single point of failure. If the Aadhaar system itself is compromised, or if there are vulnerabilities in the authentication process, it could have widespread implications for telecommunication security. Although the Unique Identification Authority of India (UIDAI) maintains a secure database, the potential for spoofing attacks, where individuals attempt to bypass biometric checks using fake identities or manipulated biometric data, remains a concern. Advanced liveness detection mechanisms are crucial but require continuous updates and sophistication to counter evolving threats.
Accuracy and Reliability Issues
While facial recognition technology has advanced significantly, achieving near human-level accuracy in controlled environments, real-world deployment across India’s diverse demographic spectrum presents challenges. Factors such as variations in skin tone, lighting conditions, facial obstructions, and aging can affect the accuracy and reliability of facial recognition systems. Research has shown that certain algorithms may underperform across different ethnicities, leading to concerns about algorithmic bias and potential wrongful denial of services. This could lead to legitimate users being unable to obtain a SIM card or facing repeated authentication failures.
Privacy Concerns and Data Minimization
The collection and storage of biometric data, even for verification purposes, raise significant privacy concerns. While the Aadhaar system is designed to minimize data exposure by only returning a “yes” or “no” for authentication, the very act of mandating its use for every SIM card transaction expands the scope of biometric data processing. Critics argue that this goes against the principle of data minimization, which suggests that only the necessary data should be collected and processed.
Operational Hurdles and Infrastructure Gaps
Implementing mandatory biometric verification nationwide presents significant operational hurdles. While urban areas may have the necessary infrastructure, rural and remote regions often lack reliable internet connectivity, consistent electricity, and widespread access to smartphones with adequate camera quality for facial recognition. The Telecom Regulatory Authority of India (TRAI) reports that approximately 44% of mobile subscribers reside in rural regions, where connectivity quality and smartphone penetration are often lower. This digital divide could create barriers for a substantial portion of the population trying to acquire new SIM cards.
Cost Implications
While the cost per Aadhaar authentication transaction is relatively low, the cumulative cost of implementing and maintaining a nationwide biometric re-authentication system for all SIM card users could be substantial. This includes costs for developing and integrating biometric modules, upgrading infrastructure in underserved areas, training personnel, and managing a robust grievance redressal system. These costs could ultimately be passed on to consumers, making mobile services more expensive.
Lack of Continuous Verification
A significant drawback of the current Aadhaar-based KYC protocols is that identity verification is primarily conducted only during the activation of the SIM card. This creates a vulnerability where SIM cards can be transferred to different users without further verification, potentially bypassing the biometric safeguards. While the new law aims to address this by making biometric authentication applicable to existing users as well, the initial point-of-sale verification still leaves a loophole for misuse if not followed by continuous re-authentication.
In conclusion, while the new SIM card rule aims to bolster national security by preventing misuse of mobile networks, it faces significant opposition due to concerns about privacy, proportionality, and potential exclusion. The drawbacks of Aadhaar-based biometric verification, including security vulnerabilities, accuracy issues, privacy concerns, operational hurdles, and cost implications, highlight the complex challenges in implementing such a widespread and mandatory system.

Aadhaar System Overview
Aadhaar, managed by the Unique Identification Authority of India (UIDAI), was launched in 2009 as a voluntary program to prevent benefit fraud and facilitate access to various government-controlled services . The system collects extensive personal data, including names, addresses, phone numbers, email addresses, photographs, and core biometrics such as 10 fingerprints and two iris scans. With roughly 1.4 billion Aadhaar numbers issued, it stands as one of the largest biometric identification programs globally. The system enables digital payments, online Know Your Customer (e-KYC) verification, e-tax filing, bill payments, and financial asset management, and has been credited with improving access to subsidies and pension payments.
Privacy Threats and Concerns
The comprehensive nature of data collected by Aadhaar presents inherent privacy risks. Critics have consistently argued that such a massive, centralized database is an attractive target for cybercriminals and raises concerns about government surveillance. The potential for “political microtargeting” and the spread of misinformation and disinformation through the linkage of Aadhaar with other databases, such as voter registration, have also been flagged. The 2022 Brookings report highlighted the program’s “insecure ecosystem, lack of data standards, and the UIDAI’s lack of transparency and accountability,” citing the Comptroller and Auditor General (CAG) of India’s findings that the UIDAI failed to properly regulate its client vendors and ensure data security.
Edward Snowden, a prominent whistleblower, criticized the system, stating that the government should be “reforming the policies that destroyed the privacy of a billion Indians” rather than investigating journalists who expose vulnerabilities. The Institute for Development and Research in Banking Technology, an affiliate of the Reserve Bank of India, labeled the Aadhaar database “a prime target,” warning that the economic and citizen loss in case of an attack would be “incalculable”.
“The journalists exposing the Aadhaar breach deserve an award, not an investigation. If the government were truly concerned for justice, they would be reforming the policies that destroyed the privacy of a billion Indians. Want to arrest those responsible? They are called @UIDAI,” said Snowden.
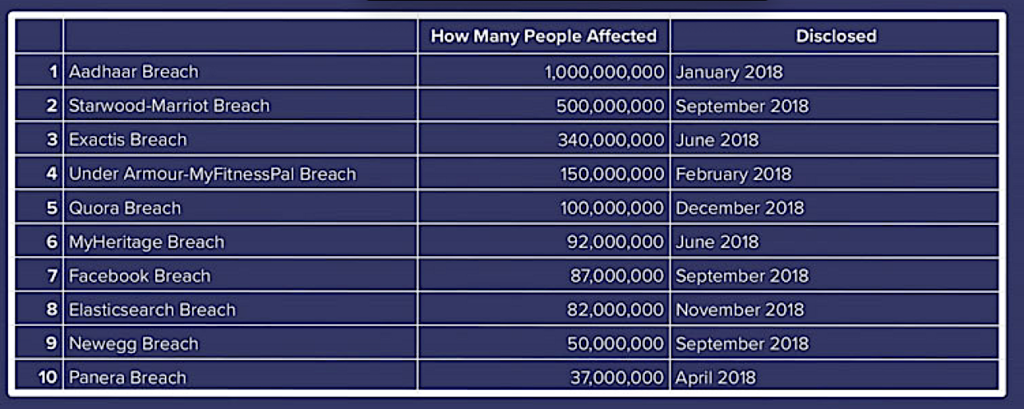
Major Data Breach Incidents and Timeline
Despite the UIDAI’s repeated assertions that the Aadhaar database is secure and has not been breached, several incidents have exposed significant vulnerabilities and led to the compromise of sensitive personal information.
2017-2018 Aadhaar Data Exposure (The Tribune Investigation)
Date of Public Exposure: January 3, 2018
In early 2018, a journalistic investigation by The Tribune newspaper revealed that unrestricted access to the Aadhaar database could be purchased for as little as 500 rupees (less than $7 USD). This was not a sophisticated hack but rather a failure of access controls, where unauthorized agents were selling login credentials that provided a gateway to the personal details of any registered citizen. The vulnerability was publicly exposed on January 3, 2018, though the access flaw may have existed for an unknown period prior.
The exposed data included names, addresses, photographs, phone numbers, and email addresses . While biometric data like fingerprints and iris scans were reported to be secure in this specific incident, the exposed PII was sufficient to enable identity theft, phishing scams, and other fraudulent activities. This incident potentially affected over 1.1 billion people enrolled in the Aadhaar system at the time, making it one of the largest data exposures ever recorded.
The UIDAI’s initial response was widely criticized. They denied a breach had occurred, calling The Tribune‘s report “misreporting,” and filed a police complaint against the journalist and the newspaper. This action sparked widespread criticism over press freedom and was seen as an attempt to “shoot the messenger”. Later, the UIDAI clarified that the FIR was not against the journalist for reporting but against the unauthorized access itself.
The technical details pointed to credential abuse and a fundamental flaw in identity and access management (IAM) within the Aadhaar ecosystem, where user privileges were not sufficiently restricted or monitored. The attack vector was simple: compromised access credentials sold through informal channels like WhatsApp.
Following the incident, the government announced new security measures, including allowing users to generate a randomly-generated virtual ID or token to avoid sharing their direct Aadhaar number for authentication, and preventing secondary agencies from storing an individual’s Aadhaar number.
State Government Website Leaks (2017)
Date of Public Exposure: May 2017 (reported)
Prior to the 2018 Tribune investigation, in 2017, it was reported that Aadhaar information of over 130 million citizens was breached through state government websites. Over 200 government websites erroneously made the database public, exposing Aadhaar numbers along with names, addresses, and bank details. The UIDAI stated that this information had been inadvertently published by other government departments and was removed once the breach became apparent.
Indane LPG System Leak (2018)
Date of Public Exposure: Reported in the months following early 2018
Another data leak was discovered in the months following early 2018, involving a state-owned utility company, Indane (LPG). Its unprotected system allowed anyone to access private information on all Aadhaar holders. The company had unlimited access to the Aadhaar database to verify user accounts, and an unprotected API endpoint through the company’s system allowed unauthorized queries to the database for potentially all Aadhaar holders.
Dark Web Sales of Aadhaar Data (2023)
Date of Public Exposure: October 2023
In early October 2023, Resecurity’s HUNTER unit identified millions of personally identifiable information (PII) records, including Aadhaar cards, belonging to Indian residents being offered for sale on the Dark Web. A threat actor, ‘pwn0001’, posted on Breach Forums, brokering access to 815 million “Indian Citizen Aadhaar & Passport” records. The data set included names, father’s names, phone numbers, passport numbers, Aadhaar numbers, age, gender, addresses, districts, pincodes, and states. Resecurity analysts validated the authenticity of some Aadhaar Card IDs using a government portal’s “Verify Aadhaar” feature.
Another threat actor, ‘Lucius’, also promoted a 1.8 terabyte data leak impacting an unnamed “India internal law enforcement organization,” which contained Aadhaar IDs, Voter IDs, and driving license records. This data set also included MSISDN, SIM activation dates, and other PII, suggesting a breach from a third-party, possibly a telecom/mobile operator.
COVID-19 Data Leak (2023)
Date of Public Exposure: June 12, 2023
In June 2023, reports surfaced indicating that several records from the CoWin database, used for COVID-19 vaccination registration, were leaked by a threat actor. This exposed personal information, including Aadhaar numbers, PAN card information, mobile numbers, and home addresses.
Indian Council of Medical Research (ICMR) Data Breach (2023)
Date of Public Exposure: October 2023
In October 2023, the Indian Council of Medical Research (ICMR) experienced a significant data breach, exposing the COVID-19 testing data of 815 million individuals. This breach included critical personal details such as names, Aadhaar numbers, passport information, phone numbers, residential addresses, and COVID-19 test results. Cybercriminals reportedly infiltrated ICMR’s extensive COVID-19 test data repository and subsequently listed the stolen data for sale on dark web forums.
Aadhaar System Vulnerability via Software Patch (2017-2018)
Date of Exploitation: Between 2017 and 2018
A series of security breaches between 2017 and 2018 exposed vulnerabilities in the Aadhaar system due to a software patch exploited by hackers. This patch, reportedly available for as little as $35, allowed unauthorized users to bypass critical security measures, including biometric authentication (iris scans and fingerprints) and GPS location tracking for enrollment operators. This meant new Aadhaar numbers could be generated from anywhere in the world without proper verification. Additionally, government websites provided unrestricted access to Aadhaar data via an API, allowing anyone with basic details like name and date of birth to check if the information corresponded to an Aadhaar number. The exposed data included sensitive information such as names, addresses, phone numbers, and biometric data.
Lessons Learned
The Aadhaar data breaches highlight several critical lessons for large-scale digital identity systems and data management:
- Principle of Least Privilege: Granting broad access to users or third-party agents is a recipe for disaster.
- Third-Party Risk Management: When vendors or partners are granted access to systems, their security posture becomes a critical concern.
- Transparency and Incident Response: Denying a breach and taking legal action against those who report vulnerabilities erodes public trust.
- Strict Access Controls and Endpoint Security: Many breaches stemmed from poorly secured APIs and vulnerable endpoints, lacking proper authentication, authorization, and rate-limiting mechanisms.
The ongoing sale of Aadhaar data on the dark web underscores the persistent threat and the need for continuous vigilance and improved security practices.
Online fraud will be Stopped? New SIM Card Rules Will Stop Cyber Crime?
Ref:
- The Aadhaar data breach wasn’t your typical smash-and-grab cyberattack. It exposed the personal information of over a billion Indian citizens, making it one of the largest data exposures in history. [ https://www.huntress.com/threat-library/data-breach/aadhaar-data-breach ]
- PII Belonging to Indian Citizens, Including their Aadhaar IDs, Offered for Sale on the Dark Web. [ https://www.resecurity.com/blog/article/pii-belonging-to-indian-citizens-including-their-aadhaar-ids-offered-for-sale-on-the-dark-web ]
- Digital Disasters: The Biggest Data Breaches of All Time. [ https://vipre.com/blog/digital-disasters-the-biggest-data-breaches-of-all-time/?srsltid=AfmBOoroI_KEH3kmDvmcdc6UVfFL8_rgSByaLLvz9mAJ3R3wpAL1w10p ]
- The Indian government has announced new security measures following reports of an alleged security breach in the country’s vast biometric database, which contains the personal details of 1.2 billion Indian citizens. [ https://www.cnn.com/2018/01/11/asia/india-security-breach-biometric-database-intl ]
- Aadhaar data breach. [ https://en.wikipedia.org/wiki/Data_breaches_in_India ]
- The personal information of more than a billion Indians stored in the world’s largest biometric database can be bought online for less than £6, according to an investigation by an Indian newspaper. [ https://www.theguardian.com/world/2018/jan/04/india-national-id-database-data-leak-bought-online-aadhaar]
- Aadhaar data breach. [ https://en.wikipedia.org/wiki/Data_breaches_in_India ]
- Data breaches in India. [https://en.wikipedia.org/wiki/Data_breaches_in_India]
- Learn about the biggest data breaches in India, why the India is an attractive target for cyber attacks and how these could have been prevented. [https://www.corbado.com/blog/data-breaches-India]
- The Indian Council of Medical Research’s Data Breach (2023). [ https://vipre.com/blog/digital-disasters-the-biggest-data-breaches-of-all-time/?srsltid=AfmBOoroI_KEH3kmDvmcdc6UVfFL8_rgSByaLLvz9mAJ3R3wpAL1w10p]
- India’s Ambitious Digital Identity System Breached Because of Old Patch. [ https://www.revelsi.com/en/blog/indias-ambitious-digital-identity-system-breached-because-of-old-patch/]
- https://m.economictimes.com/wealth/save/you-wont-be-able-to-buy-new-mobile-number-without-aadhaar-biometric-authentication-soon/articleshow/106182176.cms
- https://www.sciencepublishinggroup.com/article/10.11648/j.ajist.20250902.16
Also Read:
