The Risk of Using Biometrics
Biometrics is a science that studies physical and behavioral properties that can distinguish people from each other. The term biometric comes from two Greek words “bio” meaning life and “metric” meaning to measure.
The application of biometric systems with their simple conditions actually comes from ancient times. Relevant sources have reported that people who lived thousands of years ago identified each other with characteristics that were easily measured, such as eye colour, skin colour, and height.

The 19th-century scientist Henry Faulds proposed a paper in a “Nature” magazine about fingerprints, it recommended the use of fingerprints as a definition system, including the scientific definition of criminals.
Before the 21st century, there were time losses in the military and commercial sectors because of the lack of automatic recognition. In the early 21st century this problem got acceleration, computer technology included fingerprint recognition sensors on laptops and applied them to other intelligent devices.


In 1964, scientists Woodrow Bledsoe, Helen Chan, and Charles Bisson began working on a face recognition project. This project was called the man-machine, and the face images of people were compared with the technology of that era RAND tablets. The algorithm was designed to measure pupils, eye edges, forehead lines, and 20 parameters such as mouth width, eye width, and pupil distance.

Today’s technology has reached a stage of maturity that enables us to reveal our identity through fingerprints, voice, iris, or even through our brain print – quickly, simply, safely, without error, and in an inexpensive way. Information plays a vital role in the success of every organization, biometric information is like bits of any other digital information, and modern security industries and individuals looking for biometrics as an ideal solution. However, it can be stolen, altered even held for ransom. It is subject to all data breaches and other offences that may affect bank information or school records. Biometrics become an interesting research area in recent years, the physiological or behavioural characteristics can be used if it has these properties:
- Unique: It must be different from person to person until the twin brothers.
- Universal: It must be universal and not exist in a specific category of people.
- Durable: It should not be affected by age and be permanent.
- Measurable: Must be measurable with simple technical tools.
- Easy to use: It should be easy and convenient to measure.
The community is not clearly understood of the risks of privacy and security in biometrics. Everyone knows that biological traits can be used to identify people.
The technology has enabled a large number of new biometric identification systems that use fingerprints, iris scans, wrist veins scanning, voice recognition and facial recognition. However, when it comes to potential invasion of privacy, these different methods are not equal. All biometric systems capture biometric data, enter that data into a database, and capture new data to run against the database looking for a match. They all work well to identify individuals using computer analysis of various body parts. It is difficult to capture most biometric data and usually requires permission or explicit knowledge to capture fingerprints, iris, vein, and other biometric data [9]. For instance, your bowels or veins may not have been checked.
Selected Biometrics Technologies
Biometric behavior solutions offer less risk than the huge misuse of physical biometric techniques. Biometric behavior techniques are currently not widely used and, therefore, will not be discussed in this document. Behavioral biometric information is also much more likely collected without the user’s knowledge of the system and thus may present more legal and Organizational issues of business. This paper covers the basic concept of selected biometric methods for identification and authentication, including:

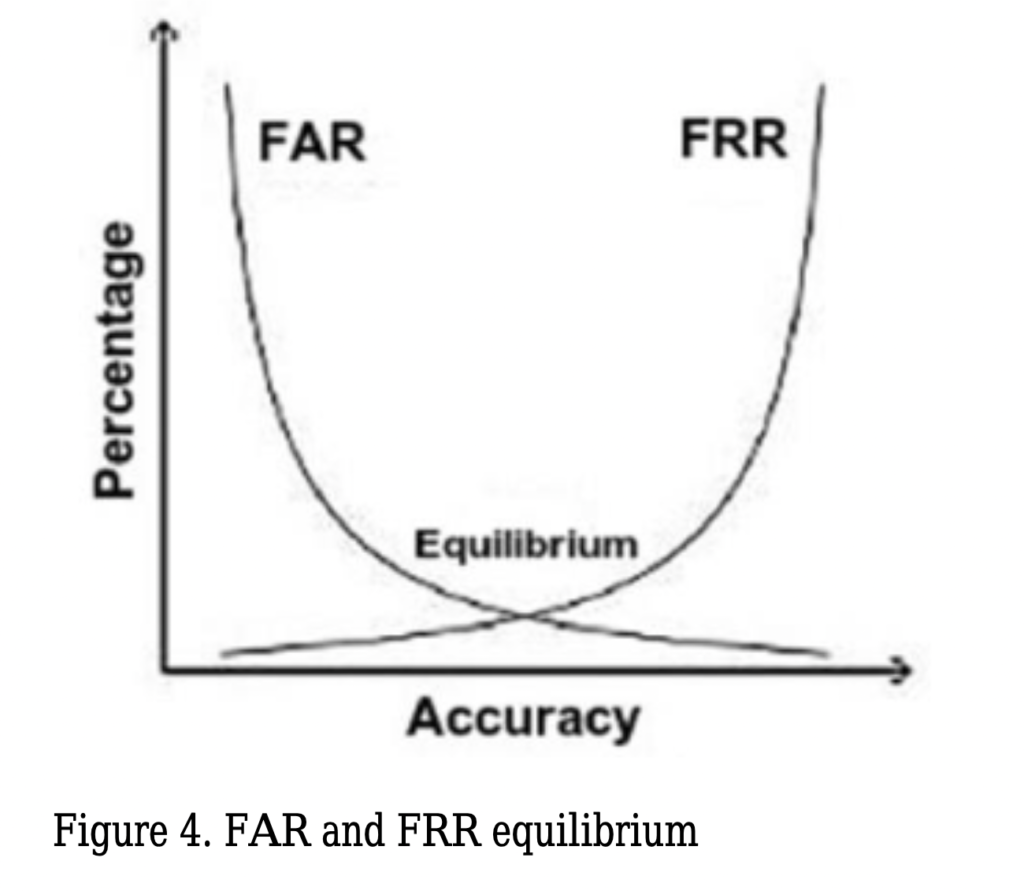
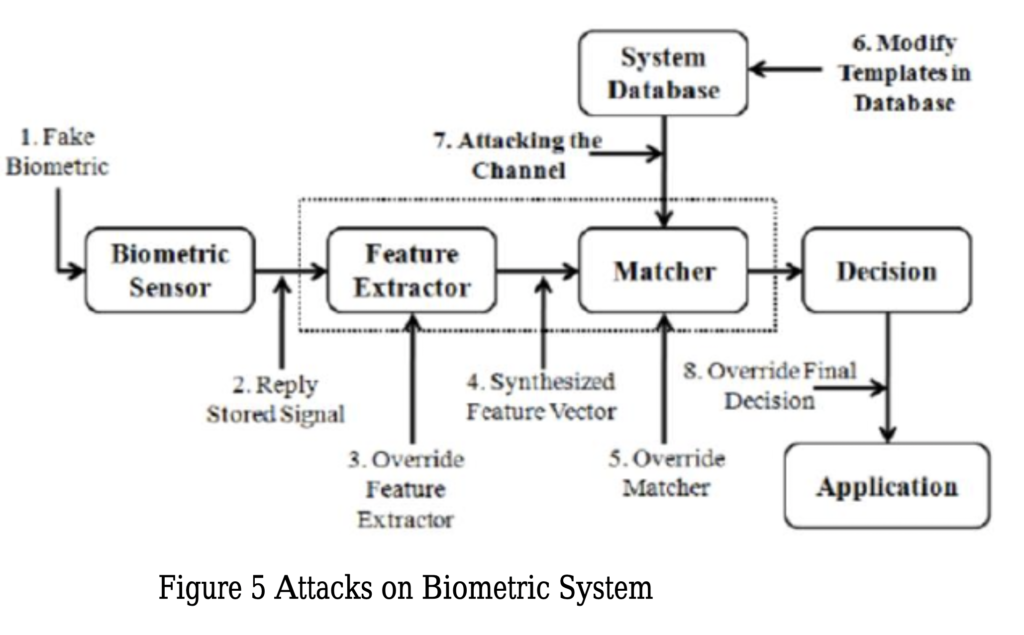
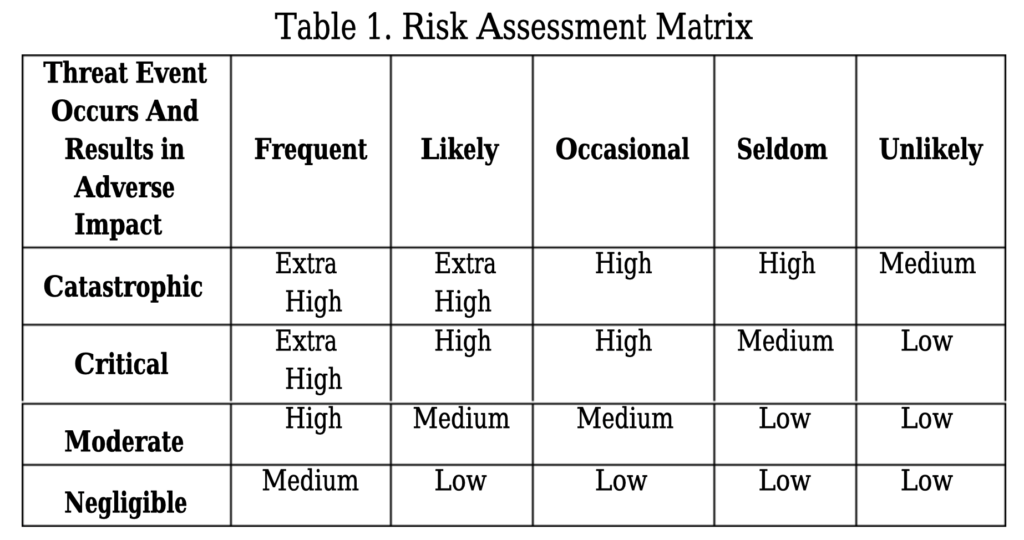
CLICK HERE 2.2 Facial recognition Facial recognition was a revolution in the biometric technology. Especially, in the last 10 years it become a popular topic. Since 2001 September 11, there has been a strong movement to integrate face Recognition techniques into national security plans. This technology can be used in monitoring activities, it has the ability to access large databases of images obtained during identification processing. This technology can be considered an easy to implement. Most of the cameras included in laptops and other portable devices are capable, with the right software, of capturing a passable facial image. Face recognition algorithms are varied, like PCA (Principal Component Analysis), ICA (Independent Component Analysis), LDA (Linear Discriminant Analysis), EP (Evolutionary Pursuit), EBGM (Elastic Bunch Graph Matching), Trace Transform Radon, Hidden Markov Model, Eigenfaces Model, Fisher Model, AAM (Active Appearance Model), Artificial Neural Networks, 3D Morphable Model, 3D Face Recognition are frequently used algorithms. Recently, face recognition algorithms have been developed by using machine learning. In 2D facial recognition techniques take recordings with a single camera and convert it to numerical value by using the algorithm that it uses. However, this may even be affected by the user’s facial expressions, environmental light, and the face. Some algorithms implement color and light normalization, but this process can extend the time for verifying the identity of the user, also increasing false negatives and false positives. Receiving more than one reference face information for a user can also fill the storage area. In addition, 2-dimensional validations can be fooled easily with a passport photo. In 3D face recognition, optical scanners map the surface it scan. Because it requires more than one camera, it increases the cost. On the other hand, color, light, and perspective have no effect on 3D techniques. Because it performs multiple 2-dimensional analysis, it provides a more accurate authentication than a single two-dimensional image. The effectiveness of all these systems can be measured. FAR (False Acceptance Rate) is the rate of false detections caused by the system’s mapping of information to a person who is not present in the database and matching it to another person in the database. False Rejection Rate (FRR) is the rate at which the system cannot find the existing person in the database. The smaller the FAR and FRR values, the closer the system is to the ideal. There is an inverse ratio between FAR and FRR. Where the FAR and FRR are equal or (the area under which the FAR and FRR curves are equal) is called EER (Equal Error Rate). The lower the EER value, the better the system. 3 Risk Factors Associated with Biometric Identification Most of the biometrics systems store the user’s data without any encryption or hashing in order to be able to access them quickly. Furthermore, those systems can be rendered ineffective due to problems caused by it, or by intentional attacks, such as a product with a high FAR due to the poor quality of the parts used can verify the wrong person or a manipulation to the sensor or database, can add a person who should not be verified. At the same time, a data of a user previously registered to the system may be copied and presented to the system in different ways. Like using the passport-size photograph of the person in 2-dimensional face recognition. Due to problems with the Face ID technology of new iPhone devices, there have been instances where the phone can be opened by children or twins. Where physical access to the device is possible, malicious users may modify the sensor to authenticate it. In the channels that provide communication between the system components, it can be performed covertly, the data can be manipulated by Man-in-the-middle attacks, brute-force attacks can be performed, the captured data can be authenticated using again and also artificial data can be generated for matching. In the case of access to the database, the confidentiality and integrity of the data in particular are compromised. Reading unencrypted data can also mean access to personal data. Similarly, the attacker can read the data, access the templates, add his own information, or change data for someone else. By altering the link between identity and biometric, it can lead to an inability to authenticate. If access to decision and matching mechanisms is available, the degree of matching of the entered value can be changed, the previously entered value can be entered again or match results can be tested and brute attack attacks can be carried out. In addition, biometric identification systems with automatic and unattended registration are always open and misleading identity. Any incorrect information to be entered at the time of registration may result in misuse or may be matched with an accurate biometric, false identification. Despite these attacks, the first important security measure is to ensure the physical security of the system. At the same time, the information in the database must be stored or encrypted. In order to solve the problems in the channels, it should be preferred that the inter-component traffic flows. Unfortunately, all these features will interfere with the performance of the device (or system). Each encryption processing can extend the time during authentication, even at machine speed. However, such measures should be taken where security and identity certainty are necessary. In addition, it is recommended that biometric verification should be used as a secondary method rather than alone, because of such problems in biometric authentication. 4. Risk Assessment and Reduction Methods In any technological intelligent systems, the risk assessment is extremely important in order to solve problems. The purpose of the risk assessment is to minimize the potential risks by calculating the probability and severity. In biometric systems, threat sources are adversarial (hackers) and non-adversarial (human errors, structural failures, or natural disasters). It is possible to determine the probability and severity of the potential attacks by considering the result of figure 5. The risk of the given process should be known correctly to make a reliable decision. In Pokorádi article, a study on fuzzy logic based risk assessment is presented which can be used in the modern complex engineering system. In the article, the author classified the risk possibilities into two categories according to their severity (catastrophic, critical, moderate, and negligible) and probability (frequent, likely, occasional, seldom, unlikely). Table 1 shows the level of risk determination from the article. Many methods can be followed to ensure using biometrics effectively and minimize the risk of using it. The first method, encrypt templates stored in databases and protect them from attackers. Therefore, digital scales can be used as a key to encrypt data until they are used. The security and authentication can be performed using the watermark method, which adds some additional information to the security object. This extra bits addition provides security to the source object. On the other hand, the source object also causes some distortion. The watermarking method includes more information to the database (data source, data destination etc.) within the data itself (image, sound etc.) this inclusion may be apparent or invisible. The purpose of using the watermark in biometrics is to confirm the data source plus detection of any change may occur. The combination of several models, several sensors and multiple biotechnologies such as fingerprints and iris can significantly reduce risks. In addition, the use of more than one biometric image sample will minimize the validation process by doing more calculations. Conclusions In this paper, the authors present a brief overview of the hidden risks of biometric techniques, some risk reduction methods and two of the most popular biometric technology fingerprint and face recognition technologies are discussed. Biometric systems face many security challenges such as system security itself, integrity, and reliability. There is a need for an information security research that addresses the specific problems of biometric systems, such as prevention of attacks based on the provision of false biometrics, reuse of previously captured biometric samples and the development of technologies. References In today’s digital age, where technology is omnipresent, the issue of privacy has become more important than ever. With the advent of biometric authentication methods, such as fingerprint or facial recognition, there is a growing concern about the potential risks these technologies pose to our personal information. However, it is crucial to note that biometrics should not be made compulsory. This article will explore the reasons why biometrics should remain optional and the importance of upholding privacy rights.Every individual has the right to control their personal information and decide how it should be used. Imposing compulsory biometrics by private sectors erodes this fundamental right, creating a susceptibility to abuse or misuse of personal data. Privacy is a fundamental human right that should be respected and protected. By making biometrics compulsory, individuals are forced to surrender their unique biological data, which can be used without their consent or knowledge. It is essential to empower individuals with the choice to decide whether they are comfortable sharing their biometric information for authentication purposes. No technology is foolproof, and biometrics are no exception. Although biometric authentication methods are touted as secure, they are not immune to vulnerabilities. Hackers and cybercriminals are continuously exploiting weaknesses in these systems, putting sensitive personal information at risk. By making biometrics optional, individuals can choose other security measures or rely on a combination of methods to safeguard their data. Another significant aspect of India’s approach to biometrics is its consideration for the vulnerable sections of society. Special provisions are made to cater to individuals who may face difficulties in providing biometric data, such as the elderly, the disabled, or those residing in remote areas. Furthermore, biometric data is not foolproof. False positives and false negatives remain a possibility, which can lead to wrongful denials of access or wrongful approval of unauthorized individuals. Such errors can have severe consequences and undermine the confidence in biometric systems. Private sectors in India are not legally bound to make biometric authentication compulsory for their services. The use of biometrics by private entities remains optional. Customers or users have the choice of whether or not they want to provide their biometrics for identification purposes. Instead of relying solely on biometrics, individuals should have the freedom to choose multi-factor authentication methods. Combining something the individual knows (like a password or PIN) with something they possess (such as a physical token or security key) provides an additional layer of security. By offering various authentication options, people can choose what works best for them without compromising their privacy. The Indian legal framework does not currently mandate private sectors to implement biometric authentication for their operations. The Aadhaar Act, passed by the Indian Parliament in 2016, primarily focuses on the usage of biometrics in government welfare schemes and public distribution systems. It does not impose any obligations on private entities to collect or use biometrics. The Act mandates the informed consent of individuals before collecting their biometric information, restricts the sharing of data with third parties, and provides individuals the right to access and correct their biometric records. While biometrics offer convenience and speed in authentication, not everyone may prefer or benefit from this technology. For individuals with disabilities or medical conditions that affect their biometric features, biometrics may prove to be more of a hindrance than a convenience. By keeping biometrics optional, we ensure that individuals have access to alternative authentication methods that are more suitable for their needs. Allowing biometrics to be optional emphasizes the importance of consent and control over personal information. Privacy regulations, such as the General Data Protection Regulation (GDPR), dictate that individuals have the right to control their data. By making biometrics compulsory, this control is compromised. By keeping biometrics optional, individuals can decide when and how their biometric data is utilized, maintaining control over their personal information. In a world where technology continues to evolve at an unprecedented pace, striking a balance between convenience and privacy becomes increasingly important. While biometric authentication methods offer efficiency and ease, they should not be made compulsory. Upholding the right to privacy, providing alternative authentication methods, and empowering individuals with consent and control over their data are essential factors that should drive our approach to biometrics. It is through this balance that we can navigate the digital landscape while protecting individual privacy in the digital age. CLICK HERE Governmental Control and Citizen Rights: Misuse of biometrics by governments can lead to the creation of a surveillance state, where individuals’ movements and activities are continuously monitored, compromising personal freedom and civil liberties. While biometric technologies can be effective in enhancing security, excessive governmental control and monitoring can erode trust, breed fear, and suppress dissent. The misuse of biometrics can allow governments to intrusively track individuals, stifling fundamental democratic principles. Another significant concern related to the misuse of biometrics is the potential for discrimination and targeted surveillance. Biometric data, when inappropriately used, can contribute to the profiling of certain individuals or groups based on race, ethnicity, religion, or other characteristics. This can result in unfair treatment, social exclusion, and exacerbation of existing inequalities. It is crucial to ensure that biometric systems are implemented and regulated in a manner that safeguards against discrimination and protects the rights and dignity of all individuals. To mitigate the risks associated with the misuse of biometrics by governments, it is essential to establish robust regulatory frameworks that govern the collection, storage, and access to biometric data. Legislative measures should include clear guidelines on data retention periods, consent requirements, and limitations on the use of biometric information. These regulations should also address issues of transparency, accountability, and oversight to prevent abuse of power. To mitigate the risks associated with the misuse of biometrics by governments, it is essential to establish robust regulatory frameworks that govern the collection, storage, and access to biometric data. Legislative measures should include clear guidelines on data retention periods, consent requirements, and limitations on the use of biometric information. These regulations should also address issues of transparency, accountability, and oversight to prevent abuse of power. Another significant concern related to the misuse of biometrics is the potential for discrimination and targeted surveillance. Biometric data, when inappropriately used, can contribute to the profiling of certain individuals or groups based on race, ethnicity, religion, or other characteristics. This can result in unfair treatment, social exclusion, and exacerbation of existing inequalities. It is crucial to ensure that biometric systems are implemented and regulated in a manner that safeguards against discrimination and protects the rights and dignity of all individuals. The potential misuse of biometrics by governments raises significant concerns regarding privacy, civil liberties, and discrimination. It is imperative to strike a delicate balance between security and individual rights by implementing comprehensive regulatory frameworks and promoting transparency. By doing so, societies can harness the benefits of biometric technology while safeguarding the essential principles that underpin democratic societies. One of the primary concerns when it comes to biometrics is the risk of unauthorized access and potential data breaches. Since biometric data is unique to each individual, a breach of this information can have severe implications. Unlike passwords or PINs, which can be changed, biometric data is permanent and cannot be easily modified. This means that if a hacker gains access to your biometric data, it could be compromised indefinitely. Another risk associated with biometrics is the occurrence of false positives and false negatives. False positives occur when a system incorrectly identifies an individual as someone else, while false negatives happen when an individual is not recognized by the system despite being a legitimate user. Both scenarios can result in inconvenience and potentially compromise security. Facial recognition technology has gained significant traction in recent years, particularly in areas such as surveillance and law enforcement. While it offers countless benefits, the use of facial recognition also raises significant privacy concerns. This technology has the potential to track individuals’ movements without their consent, leading to mass surveillance and the violation of personal privacy. Biometric data, such as fingerprints or voice patterns, can be imitated or manipulated. This opens the door to potential impersonation and fraudulent activities. As biometric data becomes more widely adopted for authentication purposes, the risk of individuals mimicking or altering someone’s biometric characteristics to gain unauthorized access also increases. Sixty-two percent of businesses in the U.S. and Europe currently use biometric identifiers for authentication, and another 24% expect to implement biometrics within the next two years. Fingerprint scanning, used by 57% of businesses, is the most popular identifier, but other methods like facial recognition are also utilized. Ref: Nearly 90% of Firms Will Use Biometrics by 2020 CLICK HERE ( https://www.infosecurity-magazine.com/news/nearly-90-of-firms-will-use/ ) Biometrics have traditionally been thought of as safer than other authentication methods, leading many businesses and organizations to move away from traditional options like passwords or adopt biometrics as a component of multi-factor authentication (MFA) protocols. However, treating biometric authentication as a cure-all for security woes poses significant concerns. Biometrics aren’t immune to attack and theft, and businesses seeking to incorporate this form of access control into their security strategies must consider the potential security and privacy risks of biometric authentication. Accurate collection of biometric data is essential for its security as a method of authentication. From a practical standpoint, incorrectly capturing data can result in access problems down the line. If the original template is incomplete or conditions during use differ significantly from the conditions under which biometrics are collected, legitimate users may find themselves unable to access systems and resources. The cybersecurity risk comes when hackers either commit fraud at the time of data collection or replace collected data with their own at a later time. This creates a scenario in which hackers can override the security of biometrics to access accounts with less risk of detection. The act of storing biometric data puts it at risk, and although security protocols offer some level of protection, the thousands of data breaches occurring in the first half of 2019 clearly show many businesses and organizations don’t have a strong enough security place. Of the 3,813 incidents reported during this time, 149 were the result of “misconfigured databases and services.” Over 3.2 billion records were exposed in these breaches alone. Ref: https://www.forbes.com/sites/daveywinder/2019/08/20/data-breaches-expose-41-billion-records-in-first-six-months-of-2019/?sh=13765082bd54 For hackers, finding an unsecured database is somewhat like being a kid in a candy store. If the database happens to be a central storage point for biometric identifiers, the results for users can be devastating. Sixty-three percent of IT professionals agree more transparency about how vendors collect biometric data is necessary so that users can be informed about the potential risks. Biometrics collected for the purpose of authentication should, in theory, only be used to identify and verify the logins of legitimate users within a network. However, neither collection nor storage of biometrics is yet subject to strict regulation outside of the consent required by the GDPR, and not all organizations collecting such data are scrupulous in their actions. Misuse of biometrics may include the unauthorized or unlawful sharing of information between third parties for use in marketing strategies or to determine specific personal details about individuals. This is especially concerning in the area of DNA profiles, which can reveal a significant amount of private information. Compromised DNA data could theoretically be used in a discriminatory manner unbeknownst to its owner. Without strong regulations in place, there’s little to stop these troubling exploitations of biometric data, and users may not have legal recourse if they discover their information has been misused. What can businesses do to protect biometric data? One solution already being implemented is to store information on user-controlled devices. When users want to log into a system, they present their credentials through an app on a smartphone or tablet, which then authenticates the login and grants access. However, the potential for device theft or loss continues to represent a major flaw in this method. Cancellable biometrics may offer an alternative and address concerns associated with the permanence of biometric data. In this method, identifiers are altered using complex mathematics into forms hackers can’t reverse. Should information become compromised during a breach, the altered biometric templates can be deleted and replaced. The algorithms can transform users’ biometrics in different ways to prevent the irreversible compromise of unique traits. Despite an increased reliance on biometrics in business and personal use cases, 90% of business owners doubt the efficacy of these authenticators as a standalone security measure. Biometrics aren’t likely to push passwords into obsolescence any time soon, either. Only 23% of IT professionals say they think biometrics will completely replace passwords for authentication in the next two or three years, which means businesses must still seek robust security solutions for the near future. No single authentication method can serve as a magic bullet to solve all security problems. As biometrics mature and authentication protocols become more sophisticated, hackers’ techniques are likely to continue to evolve in response. Businesses and organizations must look beyond the promise of a one-size-fits-all solution and create customized security plans incorporating strong authentication protocols and monitoring to ensure the highest level of protection for critical systems and data. Biometric identification systems record immutable personal characteristics in a machine-readable format. When used by governments, they can solve a hard problem: verifying personal identity in a way that cannot be faked. But in doing so, these systems create risks for the people whose data is collected, ranging from how the data is stored to what happens if the collecting agency is not in ultimate possession of the data. The risks posed by the collection and use of biometric data were disturbingly illustrated by the Taliban take-over of Afghanistan late last year, when anti-government forces seized power and inherited a powerful biometric identification system built by the U.S. military. Taliban Using Fingerprint and Gun Records to Hunt Down Afghans Who Worked for the U.S The Handheld Interagency Identity Detection Equipment (HIIDES) system was designed as a way for U.S. forces to be able to easily identify individuals in the field and tell friend from foe. But in the hands of the Taliban, these systems risked revealing the identities of individuals who had worked with American forces, potentially exposing them to reprisal. An unshakeable identification risked becoming a mechanism for revenge, punishment, or exclusion. Nearly two decades after HIIDES was first deployed by U.S. forces, the device offers an instructive look at the promises and perils of biometric identification systems, how they can be used and misused, and lessons for efforts to constrain biometric data collection. CLICK HERE In cataloging the immutable physical characteristics of a person—finger and palm prints, iris scans, facial imagery, and DNA—biometric identification systems combine multiple identifiers to produce a more complete, accurate database of identity. U.S. forces began use of biometric identification systems in Kosovo in 2001, with the BAT, or the Biometric Automated Toolset. This device combined a laptop computer, fingerprint scanner, iris reader, and digital camera used in a sit-down setting. The immediate problem BAT attempted to solve was to verify the identity of local hires, to make sure someone deemed a bad hire at one base was kept out of other bases. HIIDES was first introduced in 2005, and in 2006 HIIDES-maker Viisage won a $10 million contract from the Department of Defense for the hand-held device, on the premise that it would collect multiple kinds of biometric information in one unit, and could do so in the field. The company touted the device “for mobile identification of individuals on the battlefield, at border checkpoints, in airports, in detention centers, and for checking individuals against known watch lists.” By 2007, the device was in the hands of U.S. forces in Iraq, used to register and check the identities of candidates for police training. Individuals in the HIIDES database would be coded as green or red—green for friendly, red for a potential threat. Individuals could be enrolled in the database in a number of ways, as part of a job application, like with the Iraqi police, or by just passing through a checkpoint where soldiers were ID’ing people with HIIDES. The device could be used by soldiers on patrol, who found it more effective than asking for an identification card. In the chaos of post-invasion Iraq, HIIDES allowed the U.S. military to create from scratch a national identification system—one that could not be deceived by forged paperwork or stolen uniforms. Concerned that bases might be breached by hostile forces obtaining access as local workers, the U.S. military turned to HIIDES to ensure that only authorized and vetted people were allowed access. As the war on terror marched on, biometrics would play a key role in its administration. Once deployed in Afghanistan, HIIDES was used to confirm whether soldiers on the payroll of the Afghan National Defense Forces were showing up for duty—an effort to eliminate so-called “ghost soldiers.” The use of biometric data in a national database sits at the center of a scathing look by the MIT Technology Review into the dangers of building such a database, and then having it fall into the hands of a victorious enemy. Building such a database would prove risky. As early as 2016, the Taliban used the government’s biometric system to identify members of Afghan security forces traveling on buses hijacked by the rebel group. When the Taliban took over last year, the database had only grown to include “details on the individuals’ military specialty and career trajectory, as well as sensitive relational data such as the names of their father, uncles, and grandfathers, as well as the names of the two tribal elders per recruit who served as guarantors for their enlistment,” the MIT Technology Review reported. In using biometrics to identify their enemies, the Taliban had ripped a page straight from the U.S. military’s playbook. “Knowing who belongs in a village—who they are, what they do, to whom they are related, and where they live — all helps to separate the locals from the insurgents.” The Commander’s Guide to Biometrics in Afghanistan, published in April 2011, observes. “Targeting is enhanced through the use of biometrics by positive identification of the target.” This is the crux of biometric data. In building a tool and a database that can permanently identify every person in that database, the risk lies entirely in how the group in possession of the database uses it. The risks specific to the HIIDES device stems from its design requirements. Each HIIDES unit had finite memory capacity, with the data uploaded over secure internet connections to a central database. Storing many identities locally was an adaptation to unreliable or irregular access to internet infrastructure, making the tool useful in the field even when not online. Keeping the threshold for access below the level of classification and mandatory encryption meant that soldiers in the field could input data easily and that data could be combined with other entries without obstacle. It also meant that when the HIIDES unit and its database fell into enemy hands, there was little inherent in the technology to prevent access to the data. When the use of biometric technologies in the war on terror was being debated, there was little recognition of its risks. “Biometric identifiers are the most secure and convenient way to authenticate and identify people because they cannot be borrowed, stolen, forgotten, or forged,” Sen. Dianne Feinstein said during a November 2001 hearing. “If government does not get involved to provide some order and structure,” Feinstein continued, “then the market will result in a gradual and uneven adoption of biometric identifiers that will continue to leave our country vulnerable to terrorist attack.” The fail state, as the senator understood it 20 years ago, was not that the collected data would be used to cause harm, but that the implementation would be incomplete and harm would happen anyway. In the intervening two decades, the understanding of harm has instead shifted to what happens once the data is collected, and what rights to privacy people have regarding the collection and use of their biometric data. Recognizing these harms, localities, nations, and international organizations have moved to restrict biometric data collection, retention, and uses. The European Union’s General Data Protection Regulation, which went into effect in May 2018, prohibits the processing of biometric data for the purpose of uniquely identifying an individual, except for in certain circumstances. The act, which also includes provisions regarding data storage and security, does not prevent companies or governments from collecting biometric data and using it. Instead, it mandates rules for how that data collection can take place, while still preserving the rights of an individual, and mitigating harm to those individuals from any lost or breached data. In 2008, Illinois passed the Biometric Information Privacy Act, becoming the first state to regulate biometric data. The act sets out three principles of biometric data collection: consent from individuals in the collection of the data, the destruction of biometric identifiers in a timely manner, and the secure storage of biometric data while held by companies. The recent history of biometric identification systems has left most privacy activists convinced that the best way to prevent the harms of such systems is to not collect data in the first place. “Better protections on information and its uses can only go so far,” writes Matthew Guariglia, a policy analyst at the Electronic Frontier Foundation. “In many instances, the only way to ensure that people are not made vulnerable by the misuse of private information is to limit, wherever possible, how much of it is collected in the first place.” For the United States, a reliance on HIIDES-like systems, or biometrics in general, compounds the risk to allies and local partners in future counterinsurgency wars. Building a database to ensure the fixed identity of allies means creating a future weapon that can be used against them should the United States leave. Yet the benefits HIIDES offered for targeting and security purposes suggest that the military is likely to continue using such technology. Threats common during counterinsurgency warfare, like attacks disguised as coming from local allies, erode trust between U.S. and local forces and make counterinsurgency operations untenable. Biometrics can mitigate such risks while the United States is still actively involved in the country, but collecting the data and failing to secure it creates a future vulnerability for local allies. Encrypting data in biometric identification devices and systems might make unintended uses of such data more difficult, but encrypting data is ultimately only one aspect of the data-protection regimes required to secure such sensitive data. Biometric data collection in war zones is designed as an expediency, meeting immediate security needs with the tools at hand. Yet the data collected in the name of an immediate security concern can endure beyond the war, and even decades-long conflicts eventually end. Policymakers looking to mitigate the harm from data collection tools in the future would be wise to look at the existing record of how captured data has been contributed to harm and mandate safeguards. As technology continues to advance, ‘big brother’ governments in dictatorships and “free societies” alike continue to employ it to literally track everything their citizens are doing at every hour of the day. Take, for instance, the employment of biometrics. Hackney Foodbank, which operates five separate facilities throughout London under the umbrella of the Trussell Trust network, is a perfect example. The food bank is requiring patrons to use the Face Donate app, which, according to Reclaim the Net, “enables users to receive shopping tokens in lieu of traditional food parcels.” “By doing so, it helps the food bank cope with the surging demand without the need for additional manpower to manage supplies. However, to avail of the service, users are required to submit invasive facial scans. This doesn’t just facilitate the picking of food items from stores, but also paves the way for tracking purchases,” the outlet also reported. Silkie Carlo, the director of Big Brother Watch, has been vocal in calling for an end to this invasiveness. According to the Guardian, she said asking for sensitive biometric data in exchange for food is not sustainable. CLICK HERE As such, she told the Hackney Foodbank that “as biometric data becomes increasingly valuable, the repercussions of your users’ biometric data being lost or stolen could be catastrophic.” That’s because she said that biometric data can’t be reset or changed like a password after the data is breached and stolen. “It is for this reason that the legal threshold for processing biometric data must meet the strict requirement of necessity rather than of convenience,” Carlo added. Biometrics, the method of using an individual’s unique physical or behavioral characteristics to verify their identity, meanwhile, is rapidly becoming a popular means of authentication. While biometric authentication offers several advantages over traditional password-based authentication, such as convenience, accuracy, and security, it also poses significant privacy risks. One of the main privacy concerns associated with biometrics is the possibility of data breaches. In recent years, there have been numerous high-profile data breaches that have resulted in the theft of personal information, including biometric data. Unlike passwords, as Carlo pointed out, biometric data cannot be changed if compromised, making it a valuable target for cybercriminals. Once a person’s biometric data is stolen, it could potentially be used to impersonate them, gain access to sensitive information, or commit identity theft. Another privacy risk associated with biometrics is the potential for surveillance and tracking. Biometric data can be used to track an individual’s movements, behavior, and activities, raising concerns about government or corporate surveillance. Moreover, biometric data could be used to create profiles of individuals, potentially leading to discrimination based on factors such as race, gender, or ethnicity. Additionally, there are concerns about the accuracy of biometric systems, particularly when it comes to recognizing certain groups of people. For example, facial recognition technology has been shown to be less accurate when identifying people with darker skin tones or women, raising concerns about bias and discrimination. Inaccurate biometric systems could lead to false positives or false negatives, potentially causing harm to individuals who are wrongly identified or denied access to certain services. Furthermore, there are concerns about the lack of regulation and standardization when it comes to biometric data collection and storage. Unlike other forms of personal data, there are no universal standards for biometric data, making it difficult to ensure that the data is being collected and stored securely. Additionally, there are no clear guidelines on how long biometric data should be stored or who should have access to it, raising concerns about the potential for misuse or abuse. Technological advancements are one thing, but using them to control citizens or change their behaviors is unacceptable. Source: Identity Management Institute, Newstarget, Brookings, Researchgate, 100percentfedup, FoxNews, Wiley online library, Thewire, Armstrong economics, Youtube, Linkedin, Twitter, Wikipedia Amazon recently announced it’s installing pay-by-palm technology in Whole Foods stores across the country by the end of the year. “Paying with your palm via Amazon One is a pretty great experience, and customers have been ‘voting with their palms’ for many months now,” said Amazon CEO Andy Jassy. “By end of year, you won’t need your wallet to pay when checking out at any of the 500+ U.S. Whole Foods.” Amazon to add pay-by-palm tech to all Whole Foods stores by year end https://t.co/9u715FLZ3F Kim Iversen: Digital IDs To Be Rolled Out By Big Banks For WEF’s GREAT RESET Agenda The World Economic Forum (WEF) quietly partnered with Fingerprint Cards AB, the world’s leading biometrics company. The WEF has been discussing combining biometric data with financial services since at least 2016. Fingerprint Cards AB, based in Sweden, specializes in digital security and aims to make humans “the key to everything.” The company has installed programs on nearly every device, from smartphones to smart homes, and relies on personal data to access accounts. This new partnership with the World Economic Forum is intended to push forward the digital ID system in the quest for total control. The United Nations (UN) also partnered with the WEF to implement digital IDs. As their video explains, they will track you “from the day you join to the day you part.” The UN wants humanity to store all their data on their digital IDs and, as with all invasive technology, markets the program as a solution for simplicity. The World Economic Forum has long said that the push for the Great Reset would require the people to surrender their privacy. The technology from Fingerprint Card AB was the missing link. This company will use biometric data such as fingerprints, iris scans, DNA, and even inserted chip devices to link all of humanity to one centralized banking system. Going a step further, the goal of a one-world government would provide one centralized group with the power to access this data. Socrates indicates this plot will fail, but the road to failure will be long and destructive. Everyone will be linked to this global database, and it will be impossible to participate in society without joining. The WEF wants digital IDs to link to personal bank accounts for ultimate control. Gone are the days when the superior army ruled. Whoever controls the data will control everything and everyone. The Aadhaar infrastructure ecosystem has a lot of companies which were involved in creating the database and currently provide access to it for other companies through application programming interfaces (APIs). Also Read:


Why Should Biometrics be Optional?
The Right to Privacy
Data Security and Vulnerabilities
Protecting Vulnerable Sections of Society:
Alternatives to biometrics, such as the use of one-time passwords or physical identity cards, are available to ensure that no one is excluded or compromised by the mandatory requirement of biometric authentication. This inclusive approach ensures that privacy and dignity are upheld for all individuals, regardless of their circumstances.
Amazon Rolls Out Palm-Scanning Contactless Payments
Protecting Privacy in the Digital Age
Multi-Factor Authentication
The Indian Law Perspective
However, biometric data is considered sensitive personal information under the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information) Rules, 2011. These rules require private entities to obtain consent from individuals before collecting, storing, or processing their biometric data. Additionally, private entities are obligated to implement reasonable security measures to safeguard the biometric information from unauthorized access or misuse.User Convenience
Consent and Control
Discrimination and Targeted Surveillance
Striking a Balance: Regulation and Transparency
Implementing Strict Legislative Frameworks
Public Awareness and Engagement
Discrimination and Targeted Surveillance
Biometrics Risk: What Could Possibly Go Wrong?
Biometrics technology has undoubtedly revolutionized the way we identify and authenticate individuals. However, like any other technology, it is not without its risks. So what are the potential risks associated with the use of biometrics, and how can we mitigate them?Unauthorized Access and Data Breaches
To mitigate this risk, organizations implementing biometrics need to ensure robust security measures are in place. This includes encrypting biometric data during transmission and storage, implementing multi-factor authentication, and regularly updating security protocols to stay ahead of potential threats.False Positives and False Negatives
To minimize these risks, biometric systems need to continuously improve their accuracy. This can be achieved through constant refining of algorithms and regular updates to adapt to various environmental conditions or changes in an individual’s physical characteristics.Facial Recognition and Privacy Concerns
To address these concerns, it is crucial to establish clear regulations and guidelines governing the use of facial recognition technology. Limitations on data retention, consent requirements, and transparency in how facial recognition data is collected and used can help strike a balance between security and privacy.Imitation and Impersonation
To combat this risk, biometric systems need to incorporate advanced anti-spoofing measures. These include liveness detection techniques to ensure that the presented biometric sample is from a live person and not a spoofed or manipulated source.SECURITY AND PRIVACY RISKS OF BIOMETRIC AUTHENTICATION

Compromised Enrollment
Storage Risks

Privacy Problems
Potential Fixes for Security Concerns
The enduring risks posed by biometric identification systems



Knock-on consequences of biometric data collection
More businesses now resorting to BIOMETRICS so that government nannies can literally track everything you do, see and buy

(WATCH) Dystopian Biometric Payment System In Action
Fingerprint Cards AB – One BIG Step Closer to Digital IDs

